The idea of hacking Facebook is something that has crossed our minds at some point. If you have reached this article, you have probably been the victim of a Facebook hacker. And that’s when you ask yourself, how to hack a Facebook account?
The available methods are similar to those you can find to spy on Telegram or hack WhatsApp. For obvious reasons, I am not going to go into details, but I will help you recover an account affected by a Facebook hacking app. And even protect you from golden hackers.
How to hack Facebook in 2024: all the methods to protect yourself
Nowadays, hacking Facebook accounts is not available to everyone. But that does not mean that there are no applications to hack Facebook, just as there are applications to hack Instagram and even a mobile locator. Now, what should you do to protect yourself? A mix of all of the following.
How to hack a Facebook with email and without a password
If the hacker in question has access to your email, but not your password, it is likely that they will use the Forgot your password option to gain access. What this function does is send a link to the reset email, so the best thing you can do is change the password of your email client.
Hotmail, Outlook, Gmail, etc. The options are so diverse that it would be enough for another article. It is best that you opt for a strong password, with special characters, upper and lower case letters and numbers. It would also be advisable to use a password manager such as Google Authenticator or a password generator.
Browser data, a dangerous way to hack Facebook
Cookies cause and at the same time solve all problems. Surely you always hit save password when you access a social network from your computer. If the cybercriminal has physical access to your device, they only have to go to the Passwords and login section of your computer to get your data.
Is it possible if you have not physically logged in? Correct. Through a Trojan or Facebook hacking app that analyzes the content of the cookies. This is what happened to streamers like Ibai, whose access to his YouTube channel was done in this way. As? Through a malicious file sent to your email.
The best thing in these cases is to reset the browser settings or not log in with our user. Google Chrome, for example, syncs all this information across all your devices, so try accessing it in Incognito Mode or without storing your login details.
To reset it in the Google browser, paste the following link in the address bar and accept the operation:
- chrome://settings/reset
On mobile devices, you can choose to uninstall the app with all information or delete data and cache through Settings.
Beware of Facebook hacking pages
How to hack Facebook without any app? Simple, through a page or web platform. Most of these use social engineering processes. Since hacking Facebook in 2024 for free is practically impossible, these methods play with the user’s psychology. That is, they simulate the aesthetics of the social network so that you bite sooner or later.
Have you clicked on a potentially fraudulent link? What to do if you have already accessed one of these pages of dubious reliability? It is best to change the password as soon as possible. To do this, you must go to the Meta Account Center, preferably from a computer. Click here and it will take you automatically.
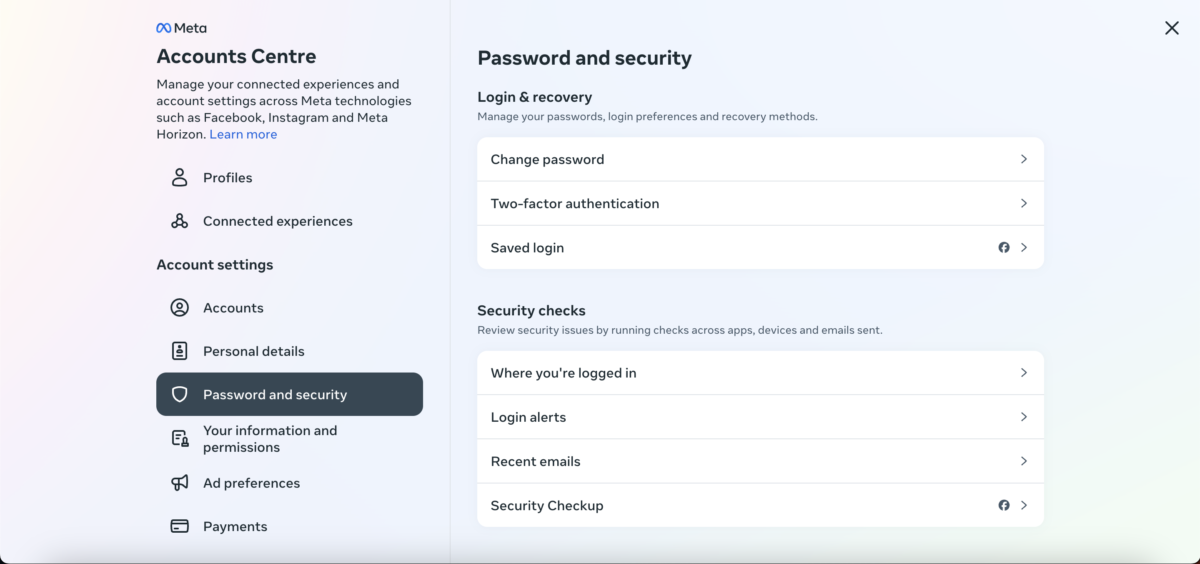
Once inside, click on the Password and Security section and then on Change Password. If the Facebook hacking page has not yet notified its manager, you can change the current password for a new one. It is also recommended to set up two-step authentication through your mobile phone or email.
You can do it in the section with the same name. You will only need to fill out the required information and indicate the numerical codes that Meta sends you through the selected verification methods.
Also with apps to hack Facebook
It’s true, there are some applications to hack Facebook accounts. In this case, they usually get remote control of the device to see everything you do with your mobile phone; This is the case with Spyzie. It is not a typical Facebook hacking application, but rather to monitor all activities from another phone.
In general, it is usually aimed at parents who want to obtain deeper control of their children’s mobile phones. But among your possible options is obtaining access to the social network without your consent. To the question, “How to hack Facebook without email and password?”, this is probably the best answer.
To do this, you need to gain physical access to the device. If you think you have any of these applications, you can go to the Applications section, within Settings, to see the complete list. Remember to click on the three dots at the top right to show all the applications, as you can see in the following screenshot:
Some are even hidden in this menu, so the only solution would be to format the phone and restore it to the factory. A hint: if you notice that system performance has declined since your suspicions began, it is likely that some hidden application has been installed.
Keylogger, the program to hack Facebook on shared computers
As its name suggests, it is software that records all your keyboard keystrokes in a text file. It was especially popular in internet cafes and public libraries, as cybercriminals gained access to dozens of accounts.

Keylogging is the easiest way to hack a Facebook password. Keylogging sometimes can be so dangerous that even a person with good knowledge of computers can fall for it. A Keylogger is basically a small program which, once installed on the victim’s computer, will record everything the victim types on his/her computer. The logs are then sent back to the attacker by either FTP or directly to the hacker’s email address.
The other reason is that it allows you to hack Facebook without a phone or email, just with a simple program. How to identify them? They usually have names like KidLogger, Revealer Keylogger or BlackBox Express. So if you find one of these in the list of programs on your PC, uninstall it immediately, although they are not always visible.
Personally, I was a victim of one of these Facebook hacking apps. The only solution? Change the password and pray it hasn’t been changed. This way, they will gain access to all our data. Facebook Dating, Facebook Marketplace. And be thankful if the golden hacker hasn’t tried to unlink Instagram from Facebook.
Now that you know how to protect yourself from all the methods to hack Facebook, you can visit other articles of interest. This one with some game hacking apps.
Other Ways Hackers can hack Facebook accounts
1. Hack Facebook Account Password By Phishing
Phishing is still the most popular attack vector used for hacking Facebook accounts. There are a variety of methods to carry out phishing attacks. In a simple phishing attack, a hacker creates a fake login page which exactly looks like the real Facebook page and then asks the victim to log in. Once the victim logs in through the fake page, the victim’s “Email Address” and “Password” are stored in a text file, and the hacker then downloads the text file and gets his hands on the victim’s credentials.
2. Stealer’s
Almost 80% per cent people use stored passwords in their browsers to access Facebook. This is quite convenient, but can sometimes be extremely dangerous. Stealers are software specially designed to capture the saved passwords stored in the victim’s Internet browser.
3. Hack Facebook Account Password By Session Hijacking
Session Hijacking can be often very dangerous if you are accessing Facebook on an HTTP (non-secure) connection. In a Session Hijacking attack, a hacker steals the victim’s browser cookie which is used to authenticate the user on a website, and uses it to access the victim’s account. Session hijacking is widely used on LAN and WiFi connections.
4. Sidejacking With Firesheep
Sidejacking attacks became common in late 2010, however, it’s still popular nowadays. Firesheep is widely used to carry out sidejacking attacks. Firesheep only works when the attacker and victim are on the same WiFi network. A sidejacking attack is basically another name for HTTP session hijacking, but it’s more targeted towards WiFi users.
5. Mobile Phone Hacking
Millions of Facebook users access Facebook through their mobile phones. In case the hacker can gain access to the victim’s mobile phone then he can probably gain access to his/her Facebook account. There are a lot of Mobile Spying software used to monitor a cell phone. The most popular Mobile Phone Spying software are Mobile Spy and Spy Phone Gold.
6. DNS Spoofing
If both the victim and attacker are on the same network, an attacker can use a DNS spoofing attack and change the original Facebook page to his own fake page and hence can get access to the victim’s Facebook account.
7. USB Hacking
If an attacker has physical access to your computer, he could just insert a USB program with a function to automatically extract saved passwords in the Internet browser.
8. Man in the Middle Attacks
If the victim and attacker are on the same LAN and a switch-based network, a hacker can place himself between the client and the server, or he could act as a default gateway and hence capture all the traffic in between.
9. Botnets
Botnets are not commonly used for hacking Facebook accounts, because of their high setup costs. They are used to carry more advanced attacks. A Botnet is a collection of compromised computers. The infection process is the same as the key logging, however, a Botnet gives you additional options for carrying out attacks with the compromised computer. Some of the most popular Botnets include Spyeye and Zeus.
Related:

