Estimated reading time: 4 minutes
There is no single way to access the deep internet. This is because the deep web is composed of several separate networks, which do not talk to each other. The best known network is Tor, open source anonymity software, which often appears in the media. Among the well-known pages is Silk Road,a drug-selling website brought down by the FBI, but which quickly resurfaced at other addresses.
What is deep web?
The deep web, also called deepnet or undernet, is a part of the web that is not indexed by search engines such as Google, and therefore is hidden from the general public – the deep internet. It is a general term for classifying several distinct site networks that do not communicate and each has its own method of access.
Generally, the deep web is associated with illegal content, such as drug sales or various other obscure activities, but the network does not only have this type of content.
The most common way to access the deep web is by using Tor, a Browser based on Mozilla’s Firefox, which connects to the network of the same name.
Through Tor, you can browse virtually anonymously through deep web sites such as Hidden Wiki, which we’ll drill down further. Before that, read more below:
How to access the deep web?
Learn how to access the deep web’s best-known network in three simple steps:
1. Download Tor
The first step is to download Tor, which has versions for Windows, Mac and Linux. The most practical way to start accessing deep web sites is to download Tor Browser, which brings a complete package with software that connects to the Tor network and a browser preconfigured to access the network, which is an adaptation of Firefox.
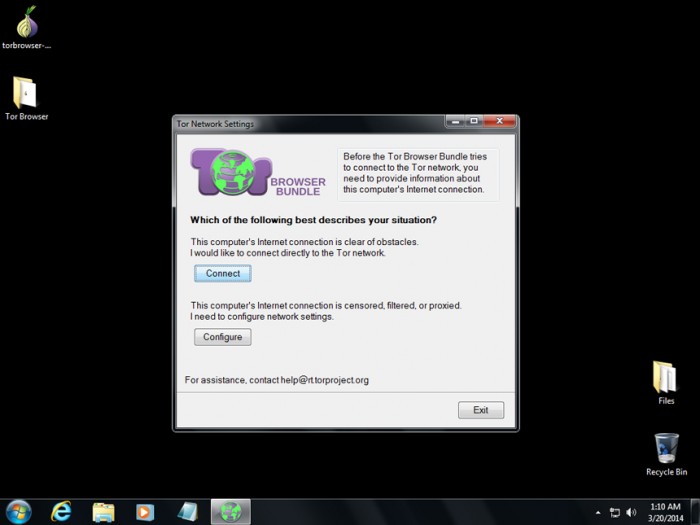
You can download Tor Browser from the official Tor Project website (torproject.org).
Just run the installer and follow the on-screen instructions. The wizard is likely to ask if you have an “obstacle-free” internet; unless you are on a censored or filtered network, just click the “Connect” button and the browser will open immediately. You are ready to access the deep web!
2. Where to start on the deep web
Because you are connected to Tor, you can browse any website through Tor Browser as anonymous. This is because, instead of directly accessing the destination site server, your computer will connect to a Tor machine, which will connect to another machine, which will connect to another machine, and so on, such as in a tunnel. The destination site will therefore receive not your IP address, but the IP of another node on the network.
But to access hidden sites on the deep web, you have to understand that you can’t find them in a conventional search engine like Google —and there’s no search engine as efficient as Google inside the deep web.
Therefore, the most common starting point is to search for a directory of sites, as if you were in the 1990s. In Tor, links are formed by random characters followed by the .onion ending.
Tor’s most famous directory is the Hidden Wiki. By Tor Browser, open the address http://zqktlwi4fecvo6ri.onion/wiki/index.php/Main_Page.
On this page, you’ll find a number of links that will take you to blogs, websites, discussion forums, and other deep web pages.
3. Deep web security recommendations
It is necessary to take some security precautions on the deep web. Because the network you are accessing is not censored, it is also full of illicit content, which could not be easily available on the internet. This includes child pornography, murder orders and the sale of unlegalized drugs. Remember that while the deep web is not censored,
governments can monitor Tor (which led to the fall of the original Silk Road) and you are responsible for the acts committed on the network.
In addition, all the security recommendations you take into consideration when accessing the internet should also be followed on the deep web—only with even more caution. Malware and undiscovered security holes may have been injected into seemingly innocent deep web pages. So it might be a good idea to create a virtual machine or use another computer before venturing out.






